Enhancing Phishing Detection: A Novel Hybrid Deep Learning Framework for Cybercrime Forensics
Enhancing Phishing Detection: A Novel Hybrid Deep Learning Framework for Cybercrime Forensics
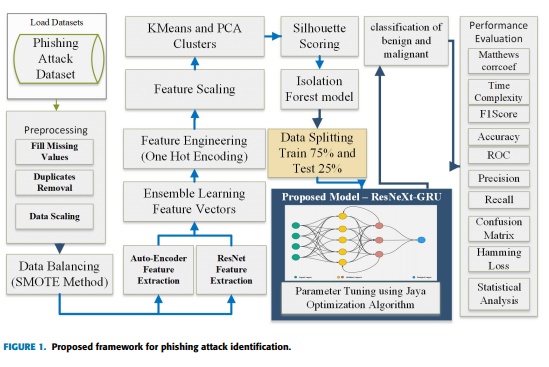
Protecting against interference is essential at a time when wireless communications are essential for sending large amounts of data. Our research presents a novel deep learning technique, the ResNeXt method and embedded Gated Recurrent Unit (GRU) model (RNT), rigorously developed for real-time phishing attack detection. Focused on countering the escalating threat of phishing assaults and bolstering digital forensics, our systematic approach involves SMOTE for managing data imbalance during initial data processing. The model’s discriminative capability is improved, particularly in the feature extraction process, when autoencoders and ResNet (EARN) are integrated with feature engineering. The ensemble technique of feature extraction reveals crucial data patterns. At the core of our AI categorization is the RNT model, optimized using hyperparameters through the Jaya optimization method (RNT-J). Rigorously tested on real phishing attack datasets, our AI model consistently outperforms state-of-the-art algorithms by a substantial margin of 11% to 19% while maintaining exceptional computing efficiency. Furthermore, our model achieves 98% accuracy, low false positive/false negative values, and a statistical execution time with a mean of 36.99s, median of 35.99s, minimum of 34.99s, maximum of 41.99s, and a standard deviation of 1.10s. Moreover, it demonstrates superior accuracy with SMOTE (98%) and without SMOTE (83%) compared to other algorithms. This state-of-the-art AI study, which focuses on digital forensics, offers enhanced security and optimized productivity for businesses and industries, signifying a breakthrough in the continuing battle against phishing attempts. Through strengthening protection against interference in wireless communication, our AI research strives to amplify data accessibility, resilience, and trustworthiness in the face of cybersecurity threats within the organizational context.
Baca juga :